What’s New
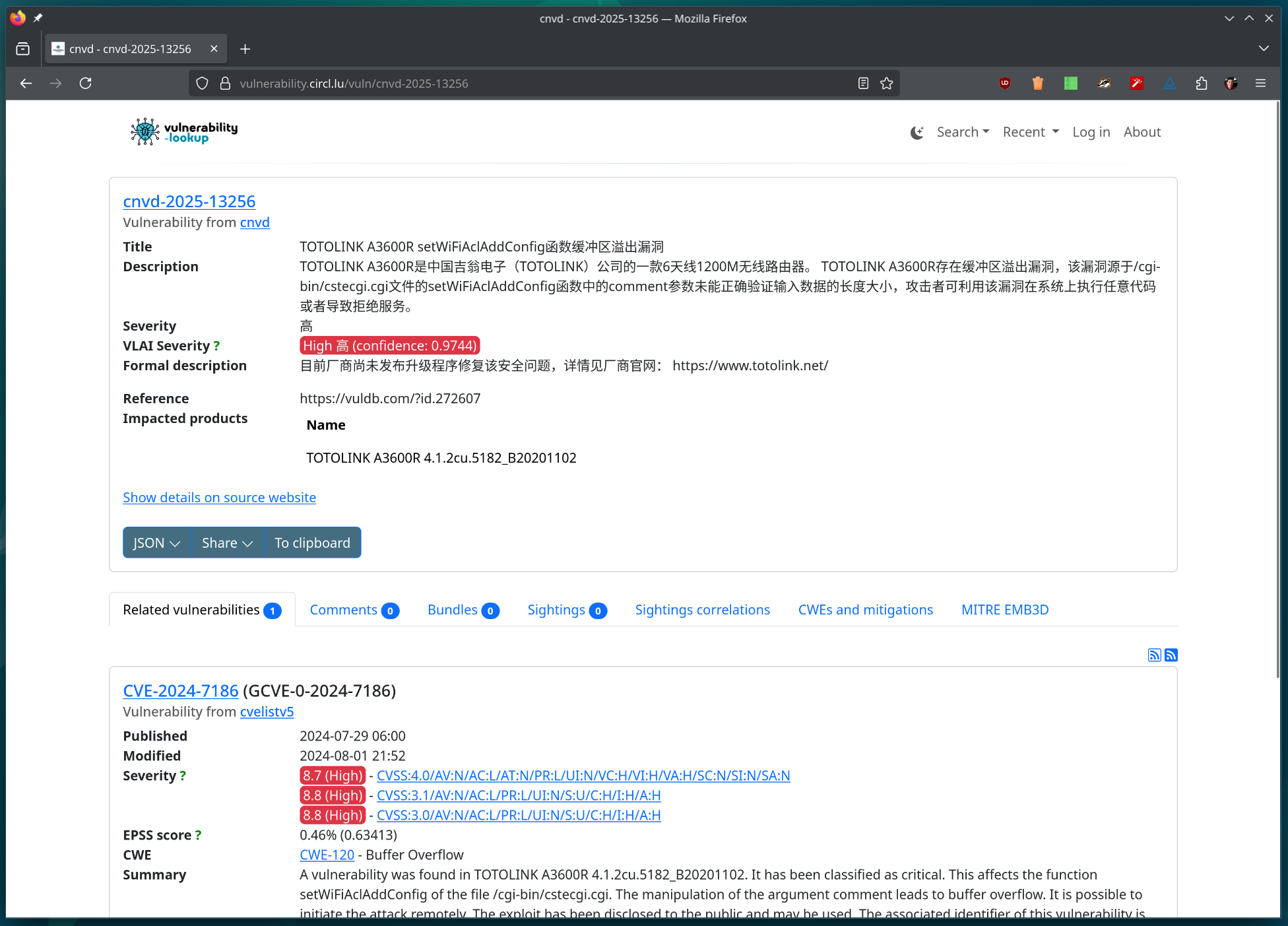
Support for VLAI Severity Classification in Chinese
For vulnerabilities originating from the CNVD source, Vulnerability-Lookup now leverages the ML-Gateway to perform inference using the CIRCL/vulnerability-severity-classification-chinese-macbert-base model.
(0b85b2d)
More information is available on VLAI Severity Classification (preprint for the 25V4C-TC: 2025 Vulnerability Forecasting Technical Colloquia. Darwin College Cambridge, UK).
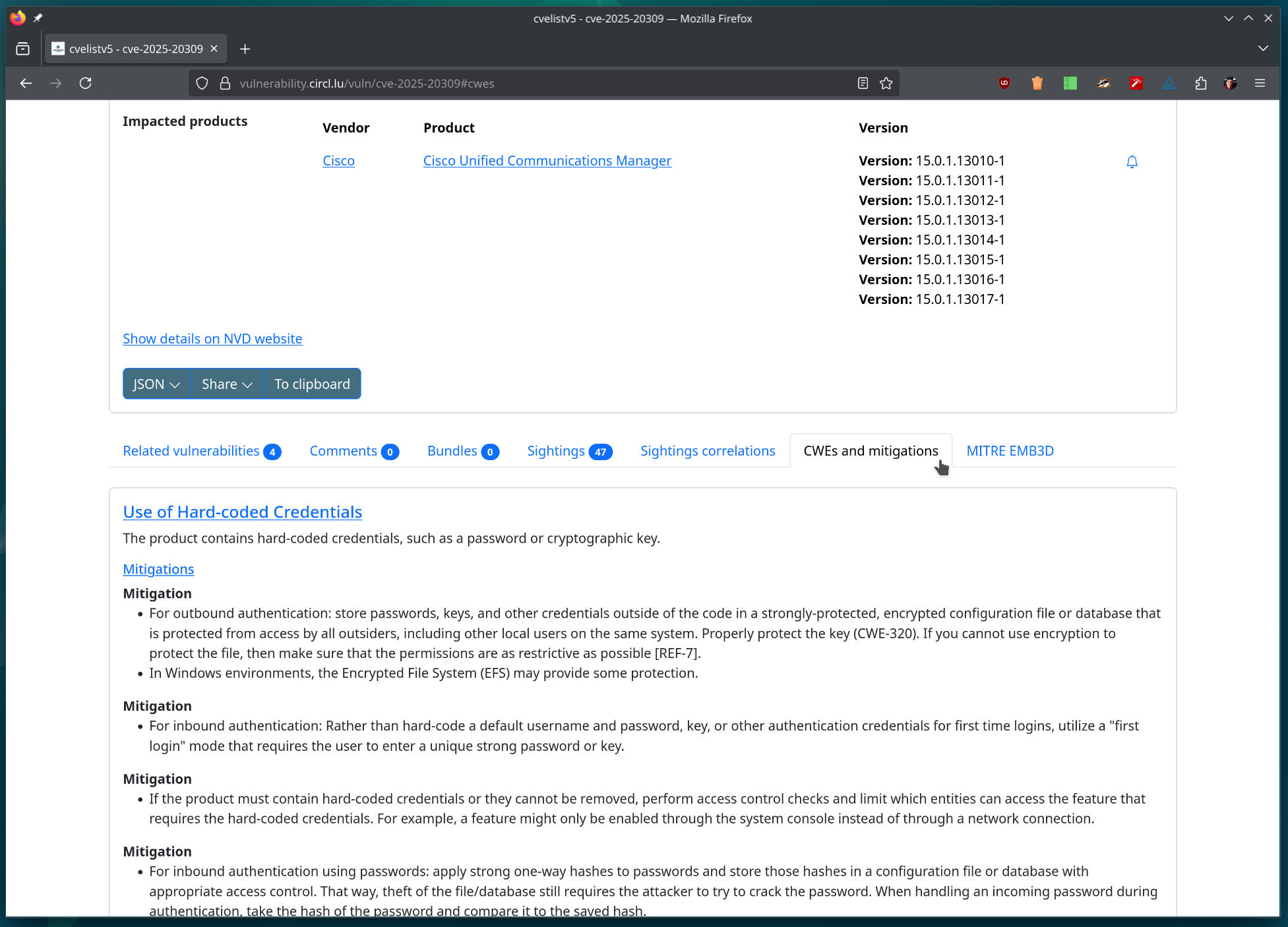
Easy Access to Mitigations from the Vulnerability View
Mitigations derived from CWEs are now directly displayed on the vulnerability details page.
(#172)
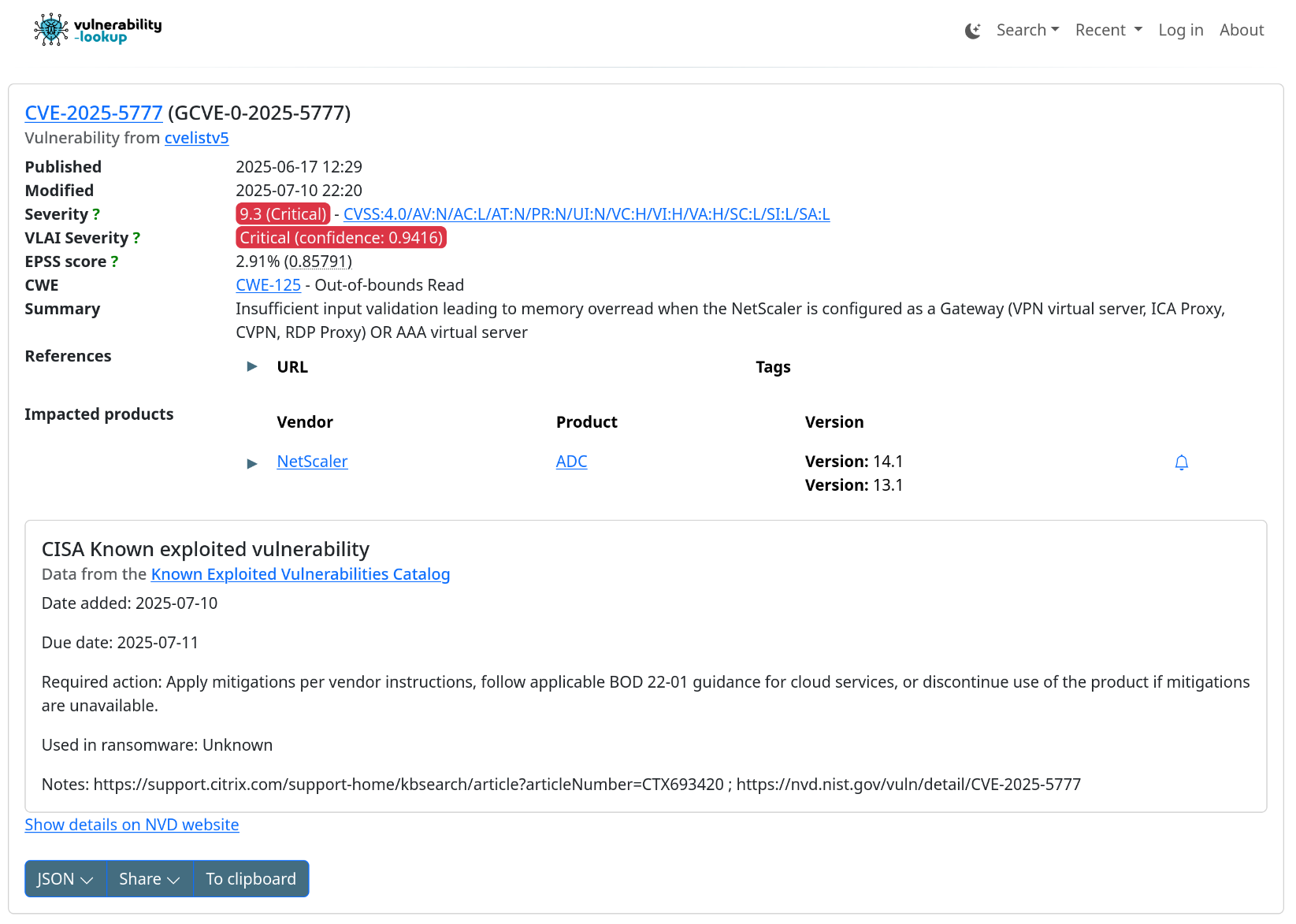
Filter Vulnerabilities by CWE via the API
The /vulnerability/last API endpoint now supports filtering results by CWE.
(#148)
Example query:
$ curl https://vulnerability.circl.lu/api/vulnerability/last/1?cwe=CWE-79 | jq .
Result:
[
{
"dataType": "CVE_RECORD",
"dataVersion": "5.1",
"cveMetadata": {
"cveId": "CVE-2006-10001",
"assignerOrgId": "1af790b2-7ee1-4545-860a-a788eba489b5",
"state": "PUBLISHED",
"assignerShortName": "VulDB",
"dateReserved": "2023-03-04T10:47:33.154Z",
"datePublished": "2023-03-05T20:31:03.187Z",
"dateUpdated": "2024-08-07T20:57:41.047Z"
},
"containers": {
"cna": {
"providerMetadata": {
"orgId": "1af790b2-7ee1-4545-860a-a788eba489b5",
"shortName": "VulDB",
"dateUpdated": "2023-10-12T08:05:39.323Z"
},
"title": "Subscribe to Comments Plugin subscribe-to-comments.php cross site scripting",
"problemTypes": [
{
"descriptions": [
{
"type": "CWE",
"cweId": "CWE-79",
"lang": "en",
"description": "CWE-79 Cross Site Scripting"
}
]
}
],
"affected": [
{
"vendor": "n/a",
"product": "Subscribe to Comments Plugin",
"versions": [
{
"version": "2.0.0",
"status": "affected"
},
{
"version": "2.0.1",
"status": "affected"
},
{
"version": "2.0.2",
"status": "affected"
},
{
"version": "2.0.3",
"status": "affected"
},
{
"version": "2.0.4",
"status": "affected"
},
{
"version": "2.0.5",
"status": "affected"
},
{
"version": "2.0.6",
"status": "affected"
},
{
"version": "2.0.7",
"status": "affected"
}
]
}
],
"descriptions": [
{
"lang": "en",
"value": "A vulnerability, which was classified as problematic, was found in Subscribe to Comments Plugin up to 2.0.7 on WordPress. This affects an unknown part of the file subscribe-to-comments.php. The manipulation leads to cross site scripting. It is possible to initiate the attack remotely. Upgrading to version 2.0.8 is able to address this issue. The identifier of the patch is 9683bdf462fcac2f32b33be98f0b96497fbd1bb6. It is recommended to upgrade the affected component. The identifier VDB-222321 was assigned to this vulnerability."
},
{
"lang": "de",
"value": "Es wurde eine problematische Schwachstelle in Subscribe to Comments Plugin bis 2.0.7 für WordPress gefunden. Hiervon betroffen ist ein unbekannter Codeblock der Datei subscribe-to-comments.php. Dank der Manipulation mit unbekannten Daten kann eine cross site scripting-Schwachstelle ausgenutzt werden. Der Angriff kann über das Netzwerk angegangen werden. Ein Aktualisieren auf die Version 2.0.8 vermag dieses Problem zu lösen. Der Patch wird als 9683bdf462fcac2f32b33be98f0b96497fbd1bb6 bezeichnet. Als bestmögliche Massnahme wird das Einspielen eines Upgrades empfohlen."
}
],
"metrics": [
{
"cvssV3_1": {
"version": "3.1",
"baseScore": 3.5,
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:U/C:N/I:L/A:N",
"baseSeverity": "LOW"
}
},
{
"cvssV3_0": {
"version": "3.0",
"baseScore": 3.5,
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:U/C:N/I:L/A:N",
"baseSeverity": "LOW"
}
},
{
"cvssV2_0": {
"version": "2.0",
"baseScore": 4,
"vectorString": "AV:N/AC:L/Au:S/C:N/I:P/A:N"
}
}
],
"timeline": [
{
"time": "2023-03-04T00:00:00.000Z",
"lang": "en",
"value": "Advisory disclosed"
},
{
"time": "2023-03-04T00:00:00.000Z",
"lang": "en",
"value": "CVE reserved"
},
{
"time": "2023-03-04T01:00:00.000Z",
"lang": "en",
"value": "VulDB entry created"
},
{
"time": "2023-03-31T12:24:01.000Z",
"lang": "en",
"value": "VulDB last update"
}
],
"credits": [
{
"lang": "en",
"value": "VulDB GitHub Commit Analyzer",
"type": "tool"
}
],
"references": [
{
"url": "https://vuldb.com/?id.222321",
"tags": [
"vdb-entry",
"technical-description"
]
},
{
"url": "https://vuldb.com/?ctiid.222321",
"tags": [
"signature",
"permissions-required"
]
},
{
"url": "https://github.com/wp-plugins/subscribe-to-comments/commit/9683bdf462fcac2f32b33be98f0b96497fbd1bb6",
"tags": [
"patch"
]
},
{
"url": "https://github.com/wp-plugins/subscribe-to-comments/releases/tag/2.0.8",
"tags": [
"patch"
]
}
]
},
"adp": [
{
"providerMetadata": {
"orgId": "af854a3a-2127-422b-91ae-364da2661108",
"shortName": "CVE",
"dateUpdated": "2024-08-07T20:57:41.047Z"
},
"title": "CVE Program Container",
"references": [
{
"url": "https://vuldb.com/?id.222321",
"tags": [
"vdb-entry",
"technical-description",
"x_transferred"
]
},
{
"url": "https://vuldb.com/?ctiid.222321",
"tags": [
"signature",
"permissions-required",
"x_transferred"
]
},
{
"url": "https://github.com/wp-plugins/subscribe-to-comments/commit/9683bdf462fcac2f32b33be98f0b96497fbd1bb6",
"tags": [
"patch",
"x_transferred"
]
},
{
"url": "https://github.com/wp-plugins/subscribe-to-comments/releases/tag/2.0.8",
"tags": [
"patch",
"x_transferred"
]
}
]
}
]
}
}
]
Changes
- Added reverse mapping support for CWEs.
(84608bb) - CWEs are now stored in dedicated kvrocks sets for vulnerabilities added through the Vulnogram interface.
(5d52048) - Improved loading mechanism for custom Jinja filters.
(f14c262) - Numerous improvements to the vulnerability details page.
- Several enhancements to the OpenAPI documentation.
Fixes
- Fixed creation and editing of notifications when the specified organization or product does not exist.
(#141) - The
POST /vulnerabilityendpoint now correctly sets vendor and product names in kvrocks for entries created via the Vulnogram web interface.
(9cc2a5b) - CSAF feeders now correctly detect and process vulnerability updates.
(49c831a)
Changelog
![]() To explore the full list of changes, visit the changelog on GitHub:
To explore the full list of changes, visit the changelog on GitHub:
![]() Thank you very much to all the contributors and testers!
Thank you very much to all the contributors and testers!
Feedback and Support
If you encounter any issues or have suggestions, feel free to open a ticket on our GitHub repository:
Your feedback is always appreciated!
Follow Us on Fediverse/Mastodon
You can follow us on Mastodon and get real time information about security advisories: